Visualizing key cyber security concepts enhances understanding and awareness of potential digital threats. Infographics simplify complex information, making it easier to recognize risks such as phishing, malware, and data breaches. Effective cyber security infographics guide users in adopting best practices to protect personal and organizational data.
The Evolution of Cyber Threats
How have cyber threats evolved over time? Cyber threats have become increasingly sophisticated, targeting both individuals and organizations with innovative attack methods. Hackers now employ advanced techniques such as ransomware, phishing, and zero-day exploits to bypass traditional security measures.
What were early cyber threats like? Initially, cyber threats mostly involved simple viruses and worms that disrupted systems or deleted data. These early attacks were relatively easy to detect and mitigate with basic antivirus software.
How did cyber threats change with the rise of the internet? The expansion of the internet introduced new vulnerabilities, leading to the rise of phishing scams and botnet attacks. These threats aimed to steal sensitive information or hijack devices for large-scale cybercrime activities.
What role do ransomware and malware play today? Ransomware encrypts victim data and demands payment for its release, causing significant financial losses. Malware now often includes spyware and keyloggers, designed to steal confidential data unnoticed.
What future trends are expected in cyber threats? Artificial intelligence and machine learning will be exploited to create more adaptive and personalized attacks. Cybersecurity strategies must evolve to counteract threats that are increasingly automated and disguised.
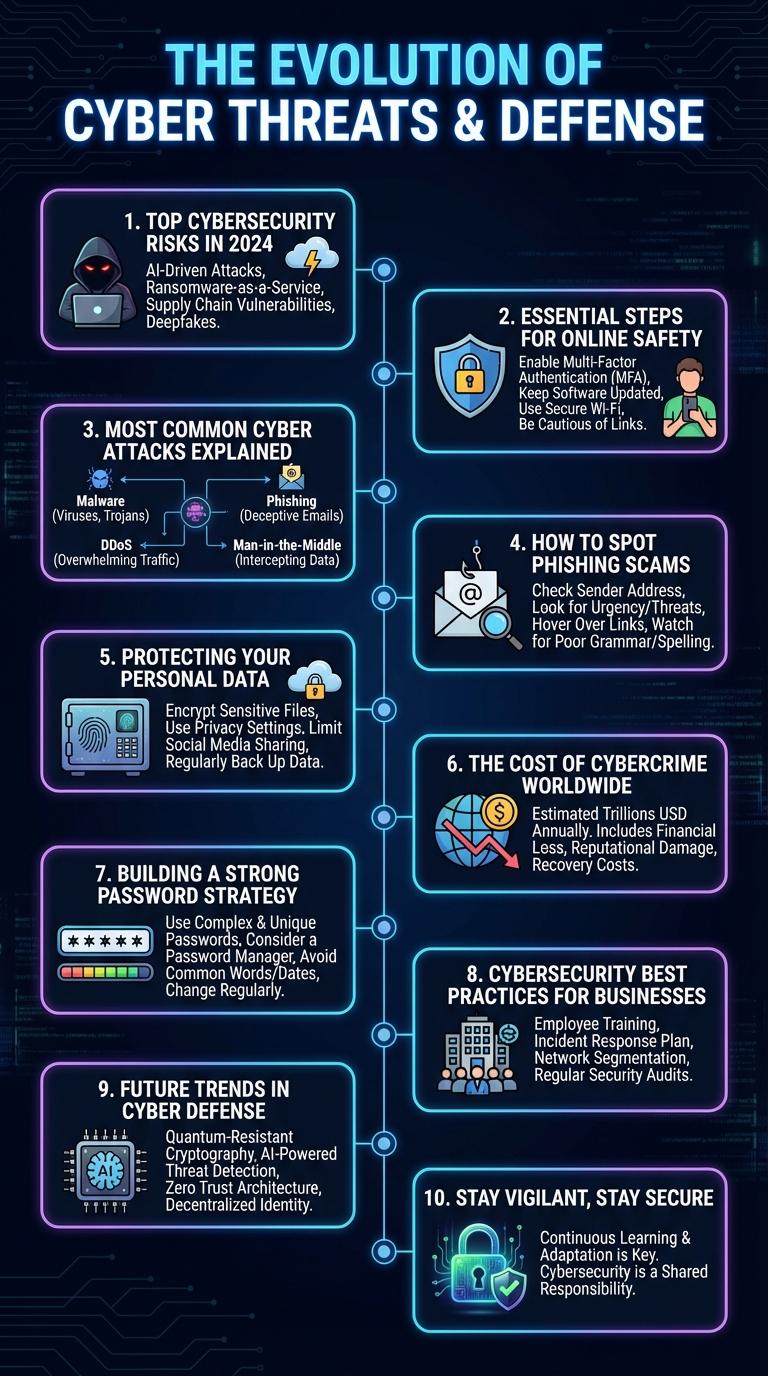
Top Cybersecurity Risks in 2024
Cybersecurity risks continue to evolve in 2024, driven by advances in technology and increasing digital interconnectivity. Understanding the top threats enables businesses and individuals to implement effective protection strategies.
Ransomware attacks remain a leading concern, with cybercriminals targeting critical infrastructure and healthcare sectors. Phishing schemes have become more sophisticated, exploiting social engineering to steal sensitive data and credentials.
Essential Steps for Online Safety
Cyber security protects your personal information and devices from digital threats. Essential steps for online safety include using strong passwords, enabling two-factor authentication, and regularly updating software. Staying vigilant against phishing scams and avoiding suspicious links further enhances your online security.
Most Common Cyber Attacks Explained
Understanding the most common cyber attacks helps individuals and organizations protect sensitive information. Cybersecurity awareness is essential to reduce the risk of data breaches and financial loss.
- Phishing - Attackers use fake emails or messages to steal login credentials or personal data.
- Malware - Malicious software like viruses and ransomware disrupts systems or encrypts data for ransom.
- DDoS Attacks - Distributed denial-of-service attacks overwhelm servers to cause downtime and disrupt services.
- Man-in-the-Middle - Hackers intercept communications to steal or alter sensitive information unnoticed.
- SQL Injection - Cybercriminals exploit database vulnerabilities to access or manipulate data.
Recognizing these attack types strengthens cyber defenses and safeguards digital assets effectively.
How to Spot Phishing Scams
Phishing scams are deceptive attempts to obtain sensitive information by impersonating trustworthy entities. Recognizing the signs of phishing can protect your personal and financial data from cybercriminals.
Look for suspicious email addresses and unexpected messages requesting personal information. Verify links by hovering over them to check their true destination before clicking. Be cautious with urgent or threatening language designed to provoke quick action.
Protecting Your Personal Data
Protecting your personal data is essential in today's digital world to prevent identity theft and privacy breaches. Implementing effective cyber security measures helps safeguard sensitive information from unauthorized access.
- Use Strong Passwords - Create complex passwords with a mix of letters, numbers, and special characters to prevent hacking.
- Enable Two-Factor Authentication - Add an extra security layer by requiring a second verification step during login.
- Regularly Update Software - Install the latest updates and patches to fix security vulnerabilities in your devices and applications.
The Cost of Cybercrime Worldwide
Building a Strong Password Strategy
Effective password strategies are essential for protecting personal and professional data from cyber threats. Strong passwords reduce the risk of unauthorized access and data breaches.
- Use Complex Combinations - Incorporate uppercase, lowercase, numbers, and special characters to create unpredictable passwords.
- Implement Multi-Factor Authentication - Add extra security layers beyond passwords to verify user identity.
- Regularly Update Passwords - Change passwords periodically to prevent prolonged exposure to potential cyberattacks.
Cybersecurity Best Practices for Businesses
Cybersecurity is essential for protecting business data and maintaining customer trust. Implementing strong password policies, regular software updates, and employee training reduces the risk of cyber threats. Businesses should also use firewalls, encryption, and multi-factor authentication to enhance security defenses.
