ICT policies establish crucial guidelines for managing technology use and safeguarding digital environments in organizations. Emphasizing data protection, cybersecurity measures, and responsible user behavior helps mitigate risks and enhance overall safety. Visualizing these policies in an infographic simplifies complex information, promoting better understanding and compliance.
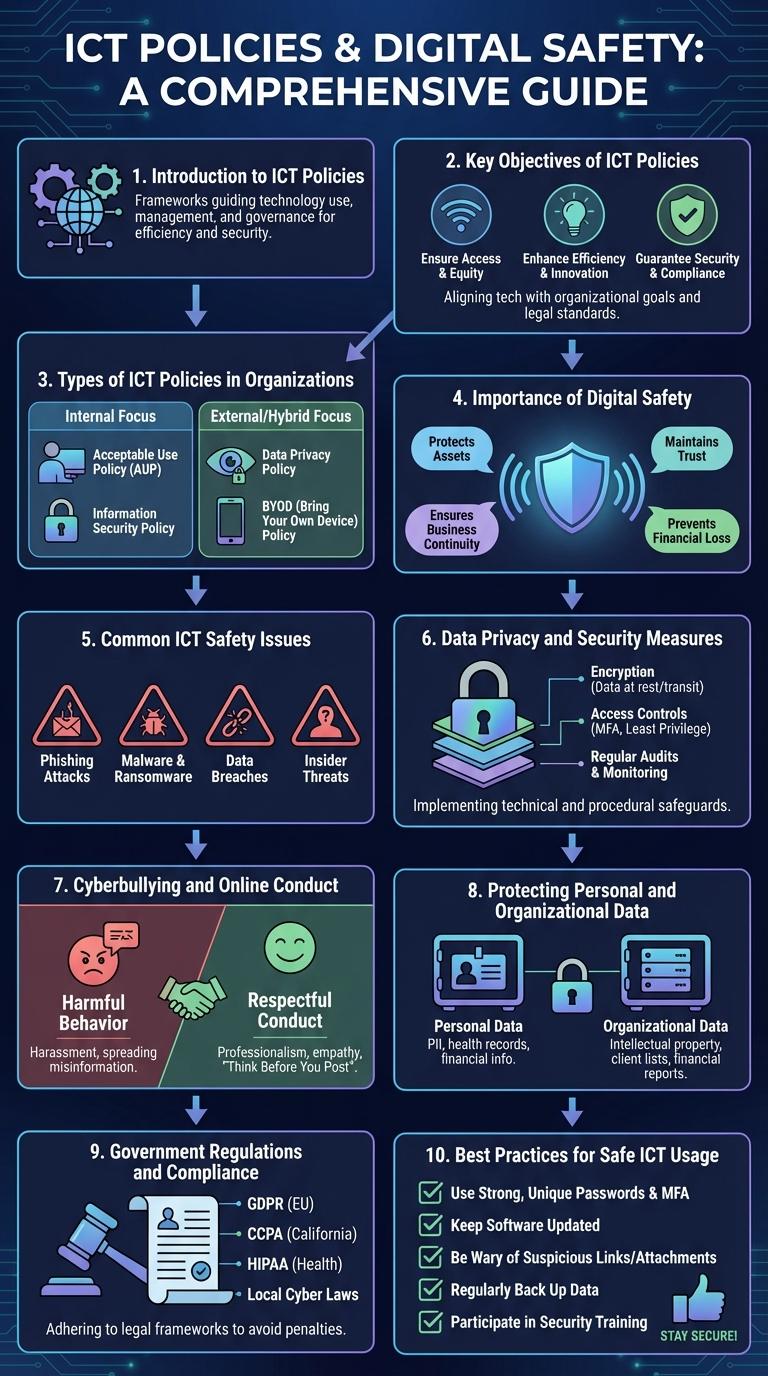
Introduction to ICT Policies
What are ICT policies and why are they critical in today's digital world? ICT policies establish guidelines that govern the use of technology within organizations, ensuring safe, ethical, and efficient operations. These policies help protect sensitive data and maintain compliance with legal standards.
How do ICT policies address safety issues? They implement security protocols such as password management, data encryption, and access controls to prevent unauthorized access and cyber threats. Such measures minimize risks like data breaches, phishing attacks, and malware infections.
What key areas do ICT policies cover in terms of safety? Policies typically include user responsibilities, acceptable use, incident response, and regular training programs. These components foster a secure environment reducing the likelihood of human error and technological vulnerabilities.
Why is regular updating of ICT policies important? Rapid advancements in technology and emerging cyber threats necessitate continuous policy review. Updating policies ensures they remain relevant and effective in protecting organizational assets and information systems.
How can organizations promote compliance with ICT policies? Clear communication, employee awareness programs, and monitoring compliance reinforce adherence to rules. Consistent enforcement helps cultivate a culture of security and accountability within the organization.
Key Objectives of ICT Policies
ICT policies guide the implementation and management of information and communication technologies within organizations. They establish protocols to enhance operational efficiency, security, and compliance across digital platforms.
- Data Protection - Ensures the confidentiality, integrity, and availability of sensitive information through robust security measures.
- Access Control - Defines user permissions and authentication methods to prevent unauthorized system access.
- Incident Response - Outlines procedures for identifying, managing, and mitigating cybersecurity threats and breaches.
- Compliance - Aligns ICT practices with legal regulations and industry standards to avoid penalties and reputational damage.
- Training and Awareness - Promotes ongoing education to equip employees with knowledge about security risks and safe technology usage.
Effective ICT policies balance technological advancement with risk management to safeguard organizational assets.
Types of ICT Policies in Organizations
ICT policies in organizations establish guidelines to ensure the secure and efficient use of technology resources. These policies help protect data integrity, privacy, and compliance with legal standards.
Common types of ICT policies include Acceptable Use, Data Protection, Security, and Software Management policies. Each policy addresses specific areas such as user behavior, data handling, network security, and software licensing to mitigate risks and promote safe technology practices.
Importance of Digital Safety
Digital safety is essential in protecting individuals and organizations from cyber threats and data breaches. Effective ICT policies ensure secure online interactions and safeguard sensitive information.
Strong digital safety measures reduce the risk of identity theft, financial loss, and privacy violations. Implementing comprehensive ICT policies fosters trust and compliance with legal standards.
- Protects Personal Data - Digital safety policies prevent unauthorized access to user information, maintaining confidentiality.
- Mitigates Cyber Threats - ICT safety protocols minimize risks from malware, phishing, and hacking attacks.
- Ensures Regulatory Compliance - Adhering to digital safety standards helps organizations comply with data protection laws like GDPR and HIPAA.
Common ICT Safety Issues
Information and Communication Technology (ICT) policies are essential frameworks designed to ensure safe and efficient use of digital resources. They address various safety issues that users may encounter while interacting with technology.
Common ICT safety issues include data breaches, malware attacks, phishing scams, unauthorized access, and software vulnerabilities. These threats can compromise sensitive information, disrupt services, and lead to significant financial losses. Implementing strong security measures and raising user awareness are critical steps to mitigate these risks effectively.
Data Privacy and Security Measures
ICT policies play a crucial role in establishing data privacy and security measures essential for protecting sensitive information from unauthorized access. These policies enforce encryption protocols, user authentication, and regular security audits to mitigate risks such as data breaches and cyberattacks. Organizations must adopt comprehensive guidelines to ensure compliance with regulations like GDPR and maintain user trust in digital environments.
Cyberbullying and Online Conduct
ICT policies play a crucial role in addressing cyberbullying and promoting safe online conduct. Effective regulations help create a secure digital environment for all users.
Cyberbullying involves using digital platforms to harass or intimidate individuals, leading to significant emotional harm. Online conduct policies guide acceptable behavior and encourage respectful interactions.
- Cyberbullying Prevention - Policies define cyberbullying and establish clear consequences to deter harmful online behavior.
- Reporting Mechanisms - Safe, easy reporting channels are implemented for victims and witnesses of cyberbullying.
- Education and Awareness - Programs promote digital literacy and responsible online engagement to reduce incidents.
Protecting Personal and Organizational Data
Government Regulations and Compliance
Government regulations on ICT policies establish standardized frameworks ensuring data protection and cybersecurity across industries. Compliance with these regulations reduces risks associated with data breaches, cyber threats, and privacy violations. Organizations must stay updated with laws such as GDPR, HIPAA, and CCPA to maintain legal and operational integrity.
